
8 Minutes
Web Security Attacks You Must Know – Part 2
Fix Bugs Faster! Log Collection Made Easy
The world is a digital place today. We fulfil most of our work, social and family tasks virtually, using the internet. The technology is now so universal, with so few barriers to entry, that practically anyone can connect to this global grid, no matter their technical skills.
However, there is a flip side. Many people lack security awareness and knowledge, which can have drastic impacts on their social and financial life. Hackers are becoming ever-more sophisticated, so it is vital that their potential victims keep learning too.
In this article, we will cover five common web applications and cyber security attacks. Even though you’ll already have a lot of technical knowledge, this information will enable you to protect yourself from these threats and maintain a robust, proactive line of defence.
What is a Web Security Attack?
Web security (or web application security) attacks are those activities performed to exploit the weaknesses and vulnerabilities of an application.
Usually, an attack involves two parties: the attacker (criminal) and the victim (user).
Attacker (Criminal)

These are the people who target a system, user or account to gain access for illegal purposes. Once they’ve gained access, they steal data, money, credentials and other essential assets. An attacker could be a human, a program or a bot, located in any part of the world.
Victim (User)

This is the person who is adversely impacted by the attacker. Anyone can fall victim to malicious online activity if they don’t take the necessary precautions; some victims are not particularly internet-savvy, but others possess a significant amount of knowledge. Victims are exposed to their attacker by the exploitable vulnerabilities of the applications they use on a daily basis.
Five Common Web Security Attacks
There are many different kinds of web security attack. They include:
- SQL Injection Attack
- Man in the Middle Attack
- Broken Access Control
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks.
- Malware
Don’t miss part 1 of this web security series, which discussed five other web security attacks. Here is the link.
Web Security Attacks You Must Know – Part 1
SQL Injection
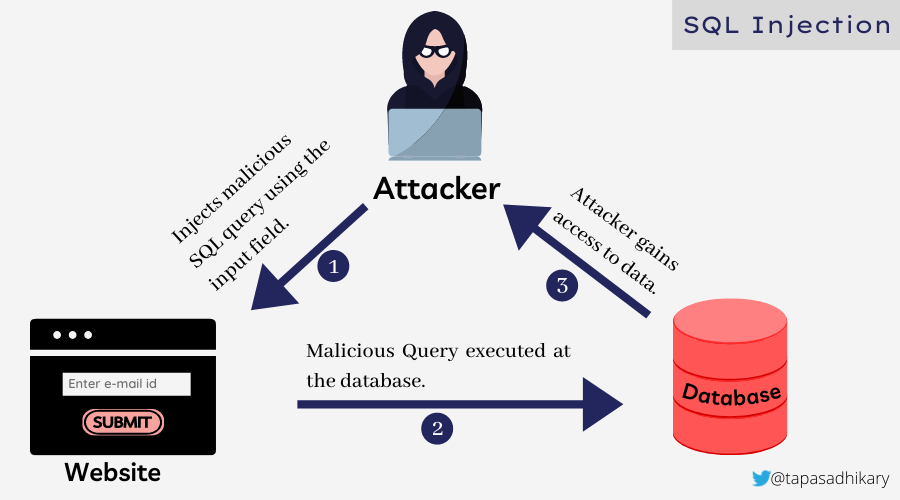
In an SQL injection attack, an attacker seeks vulnerabilities in the application’s user input validations and database configurations. The attacker injects the malicious queries using the user inputs (like textbox) to execute them on the database.
Once the execution is complete, the attacker can complete several harmful actions including:
- Stealing information.
- Dropping tables (which may allow them to delete essential records).
- Access data that should be off-limits.
The picture below shows the interactions between an attacker and a victim when the SQL injection attack occurs.
Now let’s look at a couple of examples of SQL injection attacks:
Attack using 1 = 1 kind vector which is always True
Suppose an application retrieves a customer’s account information based on a unique 6-digit PIN. The customer can type the PIN into a textbox and submit it to fetch the information from the database.
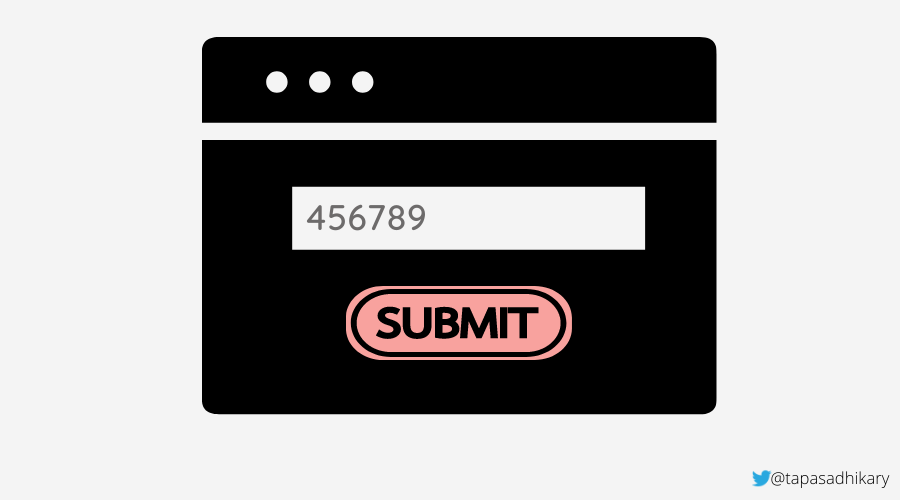
Let’s assume the PIN input value is passed to a backend service, where we construct an SQL query like this:
const sql = "SELECT * FROM Customers WHERE CustPin = " + inputCustPin;
Now, if an attacker can pass a value like 456789 or 1=1, the SQL statement will look like this:
SELECT * FROM Customers WHERE CustId = 456789 or 1=1;
So the attacker can access information about all the customer’s accounts from the database.
Attack using multiple queries execution
If an attacker is allowed to inject an entire query, the outcome can be extremely serious. It’s as bad as dropping tables, deleting important information, or misconfiguring the database. Most database applications support the execution of multiple queries as a batch.
Let’s consider a case in which the attacker posts the following string as a customer ID value: 456789; DROP TABLE Dept.
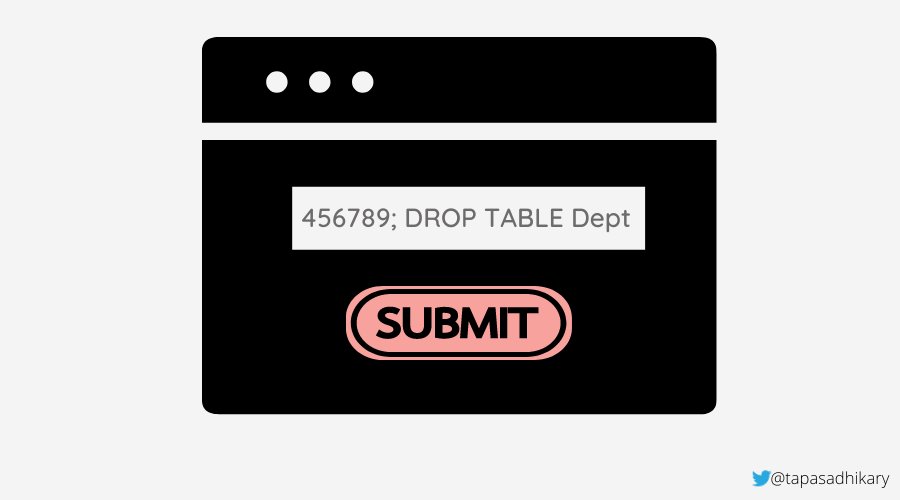
The SQL statement will be a valid one and look like this:
SELECT * FROM Customers WHERE CustId = 456789 ; DROP TABLE Dept;
Unfortunately, the above query will remove the entire Dept table from the database.
Prevention
- Most SQL injection attacks take place due to a lack of user input validations. So we must ensure that an input field only accepts the correct type of data. For example, an email field must be limited to email ids. We also need to make sure the regular SQL keywords (like DROP) are parsed out from the user inputs wherever possible.
- You can use SQL parameters in the SQL query as a prevention mechanism. These parameters are evaluated at execution time by the SQL engine, which correctly maps the parameters and also validates whether the parameter is suitable for a column.
- It’s important to always perform a scan using a web security tool, so you can assess the state of your application and know what to fix.
‘Man in the Middle’ Attack
In the Man in the Middle(MITM) attack, the attacker impersonates the legitimate user to steal vital information like login credentials, credit card details and even more sensitive data.
The victim never realizes that someone is eavesdropping on the sensitive information exchange. Equally, the end system never recognizes the attacker; it believes a legit victim is interacting.
The picture below shows how an attacker performs the role of intermediary in the communication between a victim and the target systems.
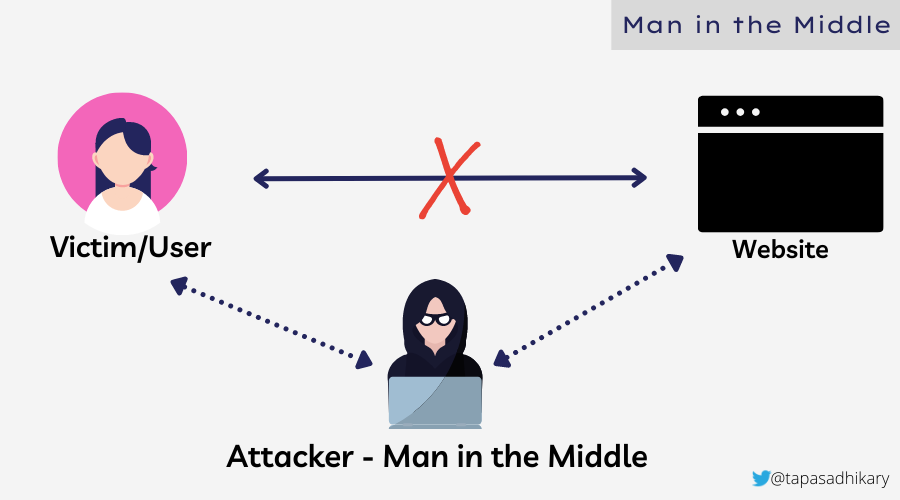
In general, a MITM attacker targets users for financial gain and identity theft. The attacker first intercepts the communication using various spoofing mechanisms like IP and DNS spoofing. After intercepting, the attacker then uses decryption methodologies like SSL Hijacking to make sense of the communication. The last stage of the attack is to pretend to be the victim and gain advantage of the attack.
Prevention
Most Man in the MIddle attacks occur due to lack of awareness of security practices. You must make sure to:
- NOT access any website that is not secured. Access sites with protocol HTTPS only.
- Not connect to a public/open WIFI, especially the password-protected one.
- Not share your sensitive information with anyone.
Broken Access Control
Access control is how you manage user access to your applications, assets and resources. It would be best to create access rules to define who is supposed to access what and, most importantly, what is not allowed. A Broken Access Control provides attackers ample opportunities to access something they are not supposed to, and then exploit it.
The picture below shows how an attacker got access to the HR database using HR role access privileges. The attacker also got access to a few ADMIN actions using misconfigured APIs.
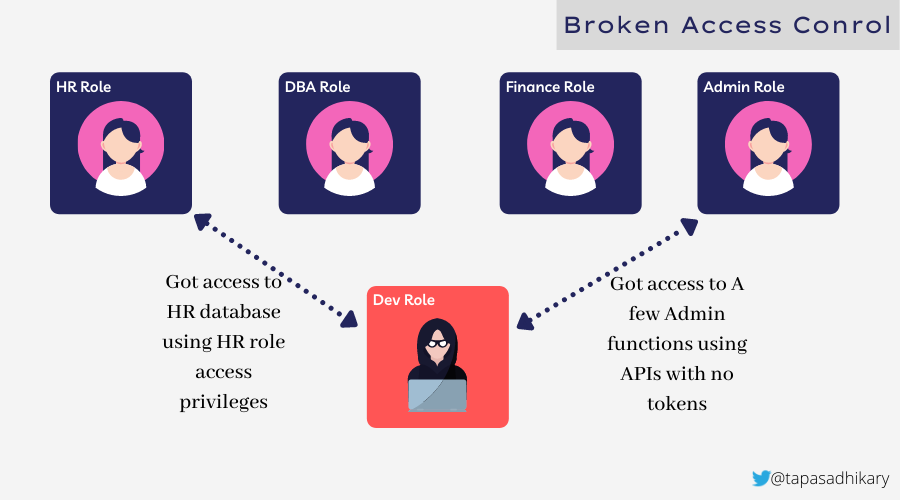
As per OWASP Top 10:2021 list:
“94% of applications were tested for some form of broken access control with [an] average incidence rate of 3.81%, and [this] has the most occurrences in the contributed dataset with over 318k.”
Prevention
You can prevent the Broken Access Control problem by making sure of the following:
- Deny all access and then allow what is required.
- Be sure to review and assess the access rights periodically.
- Adhere to the policies while elevating privileges.
- Check and validate CORS configurations.
- Guard the API access using required tokens.
Denial of Service(DoS) Attack
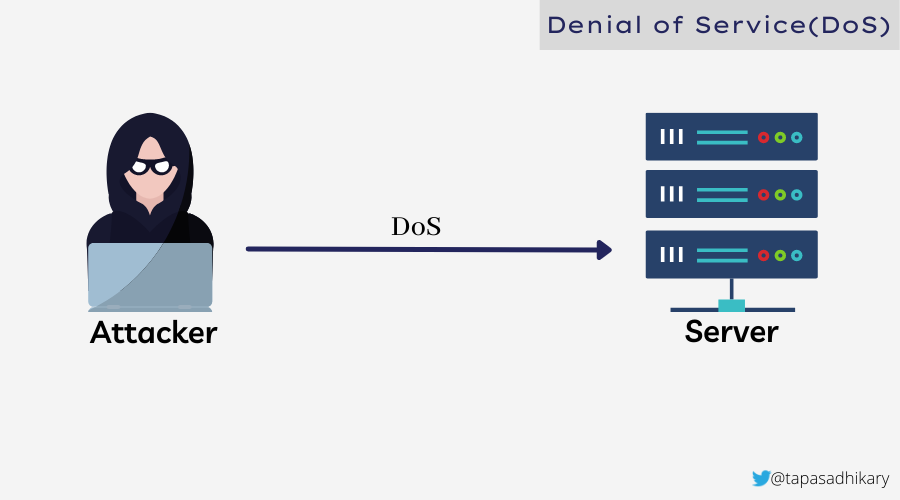
In Denial of Service(aka DoS), an Attacker targets a computer or any devices to make it unavailable to reach and use. The attacker floods the target system with a vast amount of traffic, so the target system is unable to process it. The target system eventually becomes unavailable to any new users.
An attacker may also choose to slow down the target system instead of making it unavailable. The attacker may consume all the memory in the CPU to cause a memory buffer overflow.
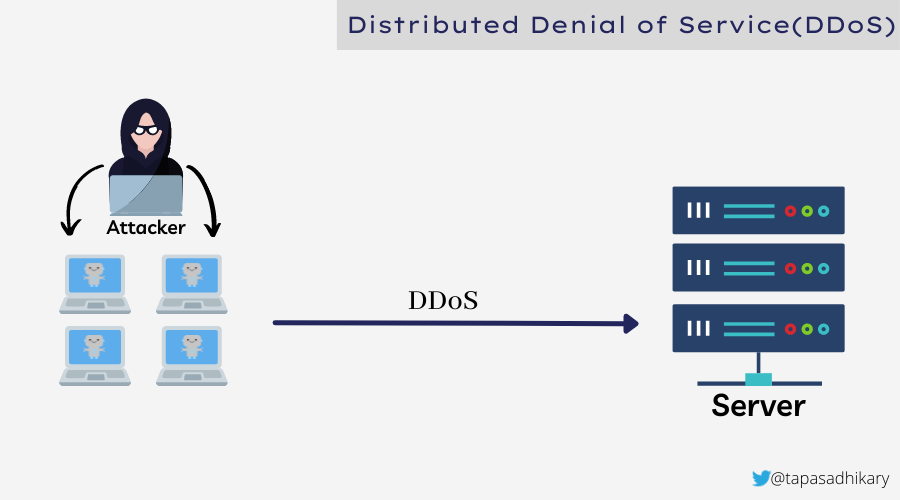
The Denial of Service(DoS) attack has another known variant called Distributed Denial of Service(DDoS). In a DoS attack, the attacker uses a single connection to the target system to initiate the attack. In the DDoS attack, the attacker uses multiple connections using a botnet to initiate the attack. DDoS is even more common than DOS.
Prevention
To prevent a DoS or DDoS attack, you must first eliminate any doubts and confirm that it is truly an attack. Your application may go sluggish due to a genuine issue, or your website may become unavailable due to a sudden surge of legitimate traffic that you were not prepared for.
However, once you identify the attack, you must try doing the following as a prevention mechanism.
- Rate limiting: this is a way to limit the incoming requests to a server, and helps prevent attackers from lodging from a vast number of requests.
- A web application firewall(WAF): this helps monitor traffic between a web app and the internet. It helps protect from DDoS and many other attacks like XSS and SQL Injection.
Malware
So, let’s discuss the last attack type, Malware.
Malware, or malicious software, is a program or code that an attacker writes and delivers over a network to infect any target devices.
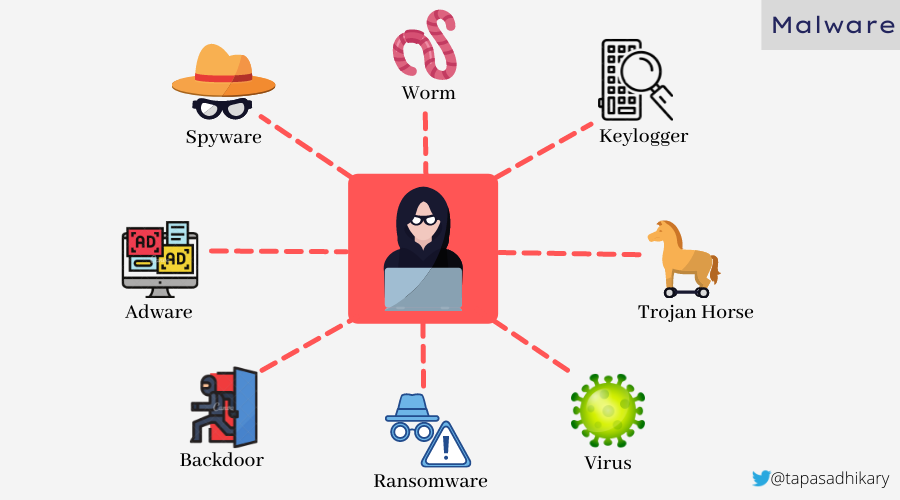
Malware can come in many forms and types. Some of the well-known types are Worm, Virus, Spyware, Adware, Trojan Horse, Ransomware, Keyloggers and Backdoor.
These attacks are intended to:
- Steal sensitive information
- Spam the target system
- Infect the system to halt essential activities.
- Blackmail the victim and demand money.
Prevention
To prevent malware you must:
- Install and activate Anti-Virus Softwares. These tools provide security from various Malware programs.
- Use the tools that come with the operating system comes w(like Windows Defender) to mitigate the risk.
Before We End…
I hope you found the article insightful! We have covered the core details of five major web security attacks. Please read more about these attacks by checking out the following links:
Expect The Unexpected!
Debug Faster With Bugfender



